Meet HIPAA Cyber Compliance requirements for processing Protected Health Information.
Evidence all 101 federal requirements of the Title 45 HIPAA Omnibus Rule for processing Protected Health Information (PHI).


What is HIPAA Compliance?
Why HIPAA Compliance?
HIPAA compliance requires healthcare organizations to establish a culture focused on protecting the privacy, security, and integrity of sensitive patient data. Adhering to these regulations not only safeguards patient information but also helps organizations avoid legal and financial penalties.
Build Patient Trust with HIPAA Compliance
FortMesa helps you prove your cybersecurity credentials internationally by:
Map Businesses Processes
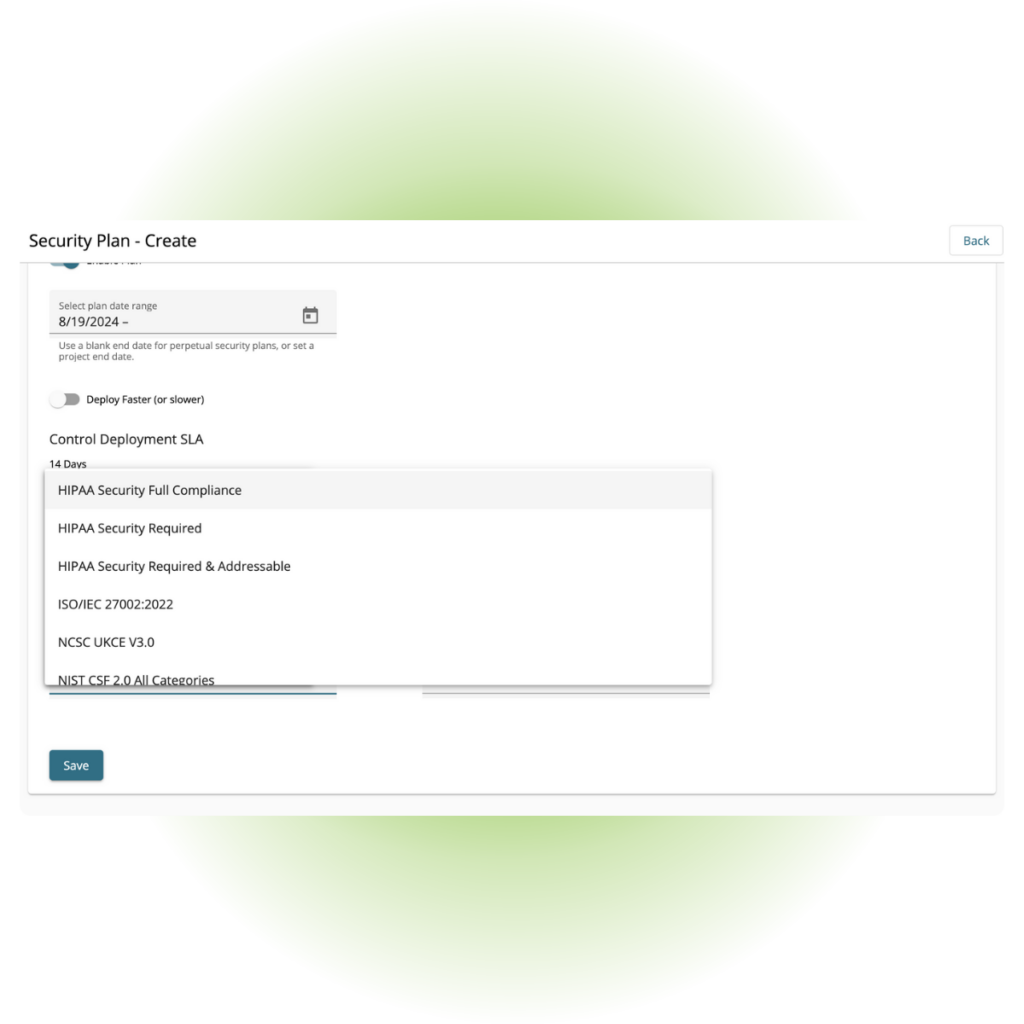
Establish security profiles that map to to meet HIPAA compliance.
Orchestrated Hardening
Choose a schedule to orchestrate system hardening over time.
Transparency Dashboard
Gain customer trust with a cyber transparency dashboard that generates always up-to-date documentation.
Grow Your Cyber Business
Use HIPAA compliance to demonstrate your expertise and reliability.
Show clients their current security status and guide them on necessary improvements.
Help clients make smart cybersecurity investment decisions.

Simplify cybersecurity service delivery
Partner Program
- Leverage industry standards and automate security planning.
- Access all-in-one solutions for compliance management.
- Build and enhance your cybersecurity services with FortMesa’s support.
Resources

Australia Cyber Security Centre Essential 8
Explore how to get your customers stop cyber attacks and get cyber compliant using the Essential Eight Maturity Model.

CIS Controls v8 Guide
The all-in-one guide on how to identifying, preventing, and responding to cyber threats, ensuring a robust security posture.
NIST CSF 2.0 Guide
Learn how to protect sensitive information, safeguard critical systems, and maintain the trust of customers and stakeholders.




