Simplify Your ISO 27001 Compliance Journey
Develop your ISO 27000 compliance strategy with FortMesa’s automated security tools.
Discover assets and vulnerabilities


Why ISO 27000 Compliance?
Security Profiles
Establish security profiles that map to industry cyber standards.
Orchestrated Hardening
Choose a schedule to orchestrate system hardening over time.
Transparency Dashboard
Gain customer trust with a cyber transparency dashboard that generates always up-to-date documentation.
leverage team security culture
- Identify Departments or Organizational Units that reflect staff hierarchy
- Add Business Processes that serve critical business functions
Invite your colleagues and coworkers to join the security process according to their role:
- Business Owner
- Organizational Unit or Business Process Owner
- Asset (Information) Owner
- Asset (Technical) Custodian
- Information Security Officer
- Information Security Engineer
Group your assets into logical units and assign them to appropriate business processes.
Notify stakeholders when a risk impacts their assets and prompt for a management action:
- Remediate the vulnerability
OR
- Accept the risk
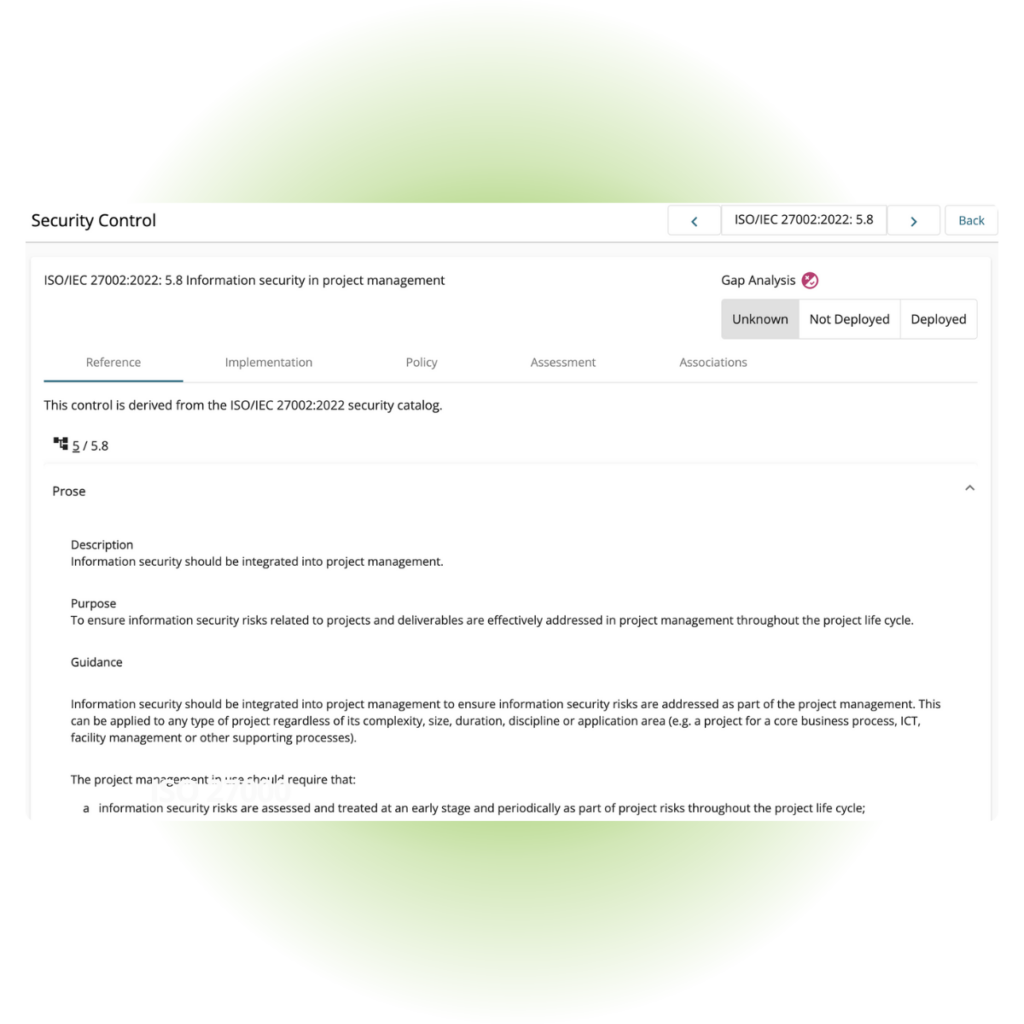

always up-to-date documentation
Resources

Australia Cyber Security Centre Essential 8
Explore how to get your customers stop cyber attacks and get cyber compliant using the Essential Eight Maturity Model.

CIS Controls v8 Guide
The all-in-one guide on how to identifying, preventing, and responding to cyber threats, ensuring a robust security posture.
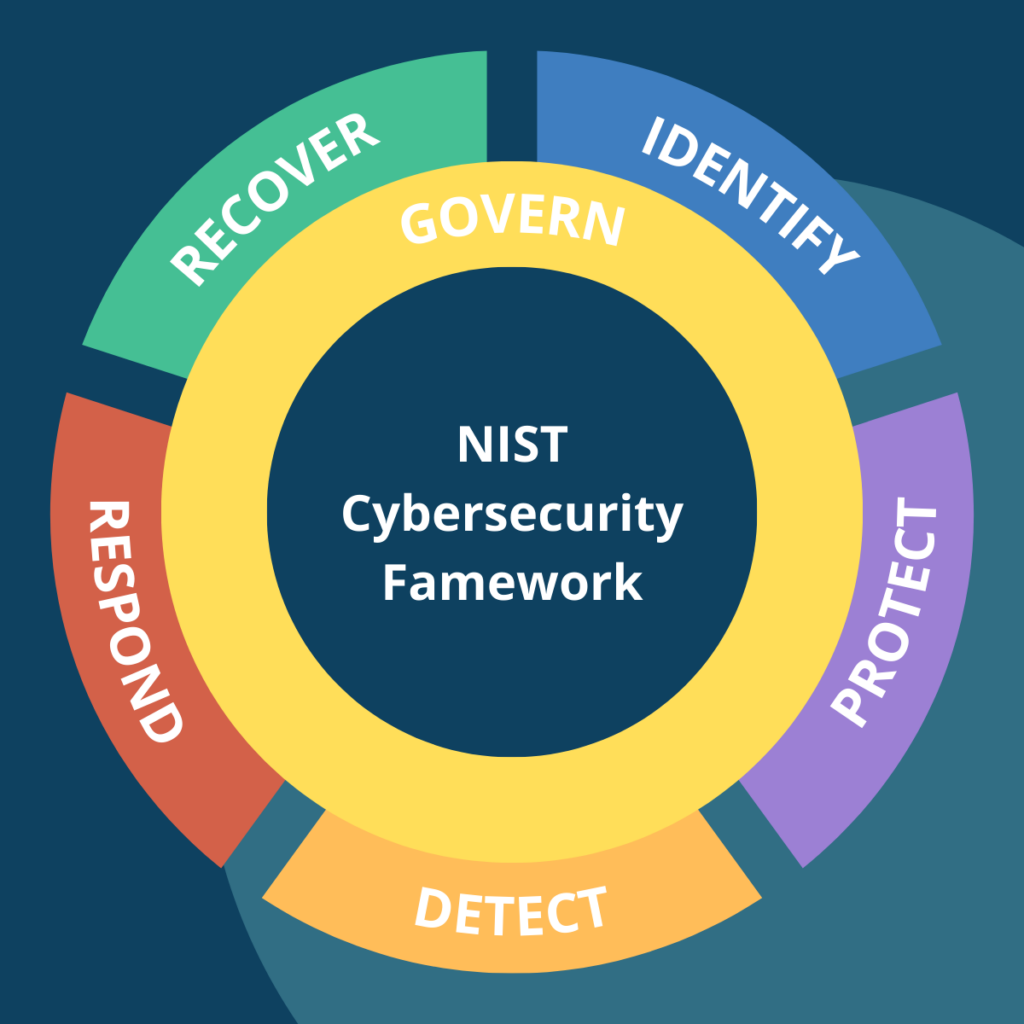
NIST CSF 2.0 Guide
Learn how to protect sensitive information, safeguard critical systems, and maintain the trust of customers and stakeholders.
Ready to Simplify ISO 27000 Compliance?
Experience how FortMesa can streamline your compliance process and enhance your cyber posture


