The Channel-First Cyber Compliance Platform
Clear Path to
Cyber Compliance
We empower IT Service Providers to deliver high-margin Compliance-as-a-Service (CaaS) and vCISO offerings.
Seamlessly Integrates With Your Stack
The Reactive Security Trap
Endpoint protection is reactive. True prevention requires eliminating vulnerabilities and building a strong foundation of cyber compliance based on proven frameworks.
Regulatory Confusion
Drowning in complex, ever-changing cyber compliance landscapes and frameworks without a clear path forward.
Third-Party Pressure
Risking lost contracts or denied insurance coverage due to strict, unavoidable security mandates.
Blind Spending
Wasting budgets on reactive tools without knowing if they actually reduce risk or meet compliance needs.
Automate cyber compliance using a
human-centric GRC workflow
Align technical remediation with recognized standards like NIST CSF, CIS Controls, and CMMC, transforming abstract security concepts into clear, actionable roadmaps that build client trust.
Discover Hidden Vulnerabilities.
Move past chasing automated alerts. Actively identify cyber vulnerabilities across the client's entire environment and baseline them against established cybersecurity standards.
Assess Business-Context Risk.
Apply deep, human-centric business context to evaluate actual threat risk, filtering out the noise to focus on critical gaps in your target compliance standards.
Align Remediation with Frameworks.
Recruit key stakeholders and map necessary technical remediations directly to strict industry frameworks (like SOC 2, HIPAA, or ISO 27001) and strategic goals.
Act on Automated Security Roadmaps.
Transform abstract framework requirements into clear, automated plans that prove ROI, verify standard adherence, and build client trust.
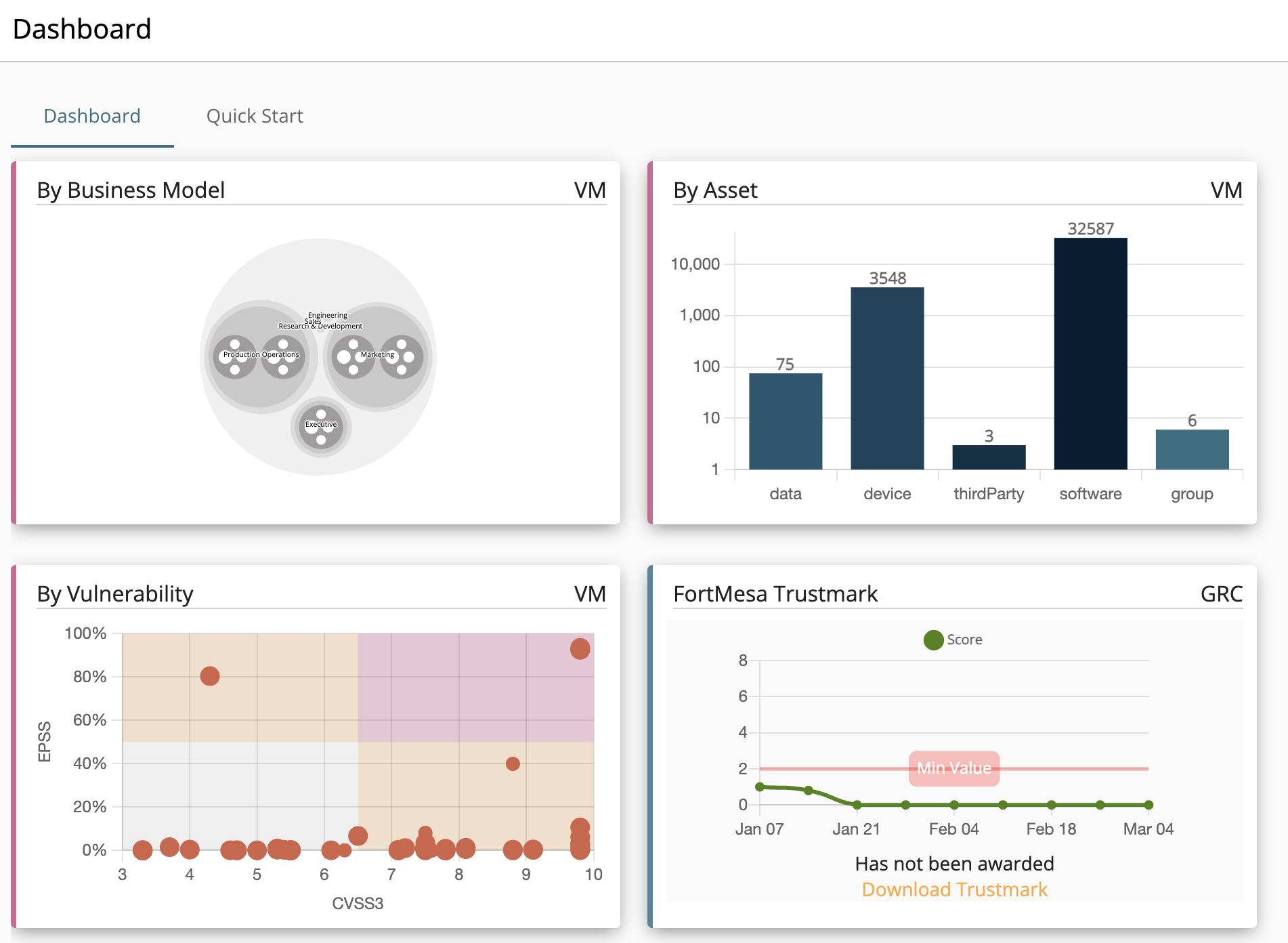
Continurisk GRC & Riskchain VM
We've unified governance, risk, compliance, and real-time vulnerability management. Stop juggling separate tools. Leverage a single engine that aligns remediation with overarching cyber compliance goals and leading security standards (NIST, CIS, CMMC):
Goal-Driven Roadmaps
Conduct control discovery and continuous assessment against any standard. Generate clear, auditor-ready evidence tailored to your client's specific framework requirements, whether it's CMMC or SOC 2.
Real-Time Scanning
Native, agent-based vulnerability scanning (Windows/Mac/Linux) feeds directly into your cyber compliance workflows to prioritize technical risks against chosen framework controls.
Scalable Deliverables
Build adaptable, repeatable cyber compliance service tiers that perfectly fit your clients' unique needs, growing alongside their security maturity and adapting to evolving regulatory standards.
One Platform. Every Standard. Every Industry.
Deliver comprehensive cybersecurity aligned with the world's leading frameworks (with CIS Controls highly recommended as a practical MSP baseline).
By Standard
Plus regional standards like UK GCHQ Cybersecurity Essentials and South Africa POPIA.
By Industry
How to Buy
We work with authorized service providers to deliver our solutions.
Operations Center
Your Command Center for MSP Cyber Compliance Delivery
Cross-Client Program Management
Streamlined client provisioning and pooled license assignment for efficient MSP operations.
Custom Cybersecurity Baselines
Create bespoke cyber compliance baselines and frameworks tailored for specific client types (often utilizing CIS Controls).
White-Labeled Security Portals
Fully white-labeled app/reports, agnostic vCISO.app access, and custom data residency.
Empowering the Future of Cyber Compliance
Profitable GRC Operationalization
Streamline operations to boost efficiency and bottom-line margins for your cyber compliance programs.
Securing Cyber Insurability
Help clients secure coverage and significantly reduce insurance premiums.
Elevating Industry Standards
Active industry collaboration with organizations like GTIA.
Scaling vCISO & CaaS Practices
Simplify compliance to successfully launch and scale highly profitable, high-value cybersecurity services.
Resources
Vulnerability Management 101
The all-in-one guide on how to stop attacks before they start using vulnerability management.
Read GuideCyber Insurance Blind Spots: Cover the Gaps
Overlooked vulnerabilities in cyber insurance, providing strategic insights to bolster coverage against cyber threats. In addition, we go over POPIA Compliance at a high level.
Watch NowCase Study: First Tracks Technology
First Tracks Technology partnered with FortMesa to automate IT security tasks, enhancing efficiency and boosting revenue by 25-30%.
Download Case StudyReady to Scale Your vCISO & CaaS Practice?
Join industry-leading MSPs who are already operationalizing GRC, securing cyber insurability for their clients, and boosting their bottom-line margins with FortMesa.




